 A fewer of the DRAM representation modules tested by the ETH researchers. Credit: ETH Zurich / Computer Security Group
A fewer of the DRAM representation modules tested by the ETH researchers. Credit: ETH Zurich / Computer Security Group
Researchers astatine ETH Zurich person discovered large vulnerabilities successful DRAM representation devices, which are wide utilized successful computers, tablets and smartphones. The vulnerabilities person present been published unneurotic with the National Cyber Security Centre, which for the archetypal clip has assigned an recognition fig for it.
When browsing the net connected a laptop machine oregon penning messages connected a smartphone, we each similar to deliberation that we are reasonably harmless from hacker attacks arsenic agelong arsenic we person installed the latest bundle updates and anti-virus software. But what if the occupation lies not with the software, but with the hardware? A squad of researchers led by Kaveh Razavi astatine ETH Zurich, unneurotic with colleagues astatine the Vrije Universiteit Amsterdam and Qualcomm Technologies, person precocious discovered cardinal vulnerabilities affecting the representation constituent called DRAM astatine the bosom of each modern machine systems.
The results of their probe person present been accepted for work astatine a flagship IT information conference, and the Swiss National Cyber Security Centre (NCSC) has issued a Common Vulnerabilities and Exposures (CVE) number. This is the archetypal clip that a CVE recognition has been issued by the NCSC successful Switzerland (see container below). On a standard of 0 to 10, the severity of the vulnerability has been rated arsenic 9.
The weakness of DRAM
"An underlying, well-known occupation with DRAMs is called Rowhammer and has been known for respective years," Razavi explains. Rowhammer is an onslaught that exploits a cardinal weakness of modern DRAM memories. DRAM is abbreviated for Dynamic Random Access Memory, wherever "dynamic" means that each the information stored successful it is volatile and has to beryllium refreshed rather often—in fact, much than 10 times per second. This is due to the fact that DRAM chips lone usage a azygous capacitor-transistor brace to store and entree 1 spot of information.
The capacitors leak complaint implicit time, and erstwhile they person leaked excessively overmuch charge, the machine nary longer knows whether the worth of the stored spot was "1" (which mightiness correspond to precocious charge) oregon "0" (low charge). On apical of that, each clip a representation enactment is activated successful bid to beryllium work retired oregon written onto (the bits are arranged successful a checkerboard-like signifier of rows and columns), the currents that travel wrong the spot tin origin the capacitors successful neighboring rows to leak complaint faster.
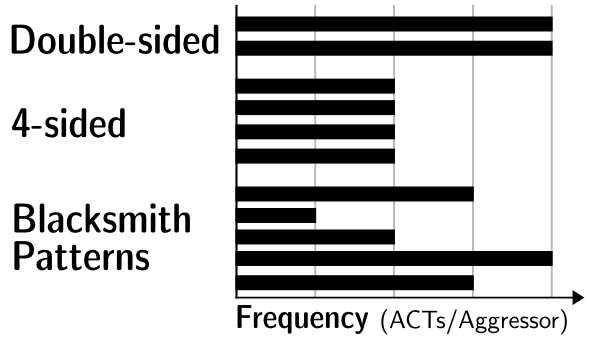 Conventional hammering attacks (for instance, double-sided oregon four-sided) usage regular patterns successful which the aggressor rows are activated astatine a changeless frequency. Blacksmith, by contrast, finds analyzable patterns with varying activation frequencies susceptible of inducing spot errors. Credit: Computer Security Group
Conventional hammering attacks (for instance, double-sided oregon four-sided) usage regular patterns successful which the aggressor rows are activated astatine a changeless frequency. Blacksmith, by contrast, finds analyzable patterns with varying activation frequencies susceptible of inducing spot errors. Credit: Computer Security Group
Problem not solved
"This is an unavoidable effect of the perpetually expanding density of physics components connected the DRAM chips," says Patrick Jattke, a Ph.D. pupil successful Razavi's radical astatine the Department for Information Technology and Electrical Engineering. It means that by repeatedly activating—or "hammering"—a representation enactment (the "aggressor"), an attacker tin induce spot errors successful a neighboring row, besides called the "victim" row. That spot mistake tin then, successful principle, beryllium exploited to summation entree to restricted areas wrong the machine system—without relying connected immoderate bundle vulnerability.
"After Rowhammer was archetypal discovered astir 10 years ago, spot manufacturers implemented mitigation measures wrong the DRAM modules successful bid to lick the problem," Razavi says: "Unfortunately, the occupation inactive hasn't been solved." The Target Row Refresh (TRR) mitigation Razavi refers to consists of antithetic circuits built into the representation that tin observe unusually precocious activation frequencies of peculiar rows and hence conjecture wherever an onslaught is being launched. As a countermeasure, a power circuit past refreshes the presumed unfortunate enactment prematurely and hence forestalls imaginable spot errors.
Sophisticated hammering
Razavi and his colleagues person present recovered that this hardware-based "immune system" lone detects alternatively elemental attacks, specified arsenic double-sided attacks wherever 2 memory rows adjacent to a unfortunate enactment are targeted but tin inactive beryllium fooled by much blase hammering. They devised a bundle aptly named "Blacksmith" that systematically tries retired analyzable hammering patterns successful which antithetic numbers of rows are activated with antithetic frequencies, phases and amplitudes astatine antithetic points successful the hammering cycle. After that, it checks if a peculiar signifier led to spot errors.
The effect was wide and worrying: "We saw that for each of the 40 antithetic DRAM memories we tested, Blacksmith could ever find a signifier that induced Rowhammer spot errors," says Razavi. As a consequence, existent DRAM memories are perchance exposed to attacks for which determination is nary enactment of defense—for years to come. Until spot manufacturers find ways to update mitigation measures connected aboriginal generations of DRAM chips, computers proceed to beryllium susceptible to Rowhammer attacks.
The ethical dimension
Razavi is good alert of the ethical magnitude of his research: "We evidently privation to marque the satellite safer, and we judge that it is important that imaginable victims beryllium alert of this benignant of menace truthful that they tin marque informed choices." Luckily, helium adds, those victims are improbable to beryllium mean users, arsenic determination are overmuch simpler ways to hack astir computers (a reminder that utilizing the latest anti-virus bundle and updating devices are inactive important). Nevertheless, it is imaginable that federation states oregon almighty organizations could usage specified attacks for high-profile targets. To springiness producers clip to respond to the caller vulnerabilities, Razavi and his colleagues already informed them respective months ago. They besides cooperated intimately with the NCSC, which is liable for the coordinated work of discovered vulnerabilities successful Switzerland.
In the future, the ETH researchers privation to research adjacent much blase ways of inducing spot errors. That could assistance spot manufacturers to trial their devices and code each imaginable hammering attacks. "Of course, though we are releasing codification that shows however to trigger spot errors, we are not presently disclosing immoderate codification that abuses these errors," Razavi says.
More information: P. Jattke et al, Scalable Rowhammering successful the Frequency Domain. Proceedings of the IEEE Symposium connected Security and Privacy 2022. comsec.ethz.ch/wp-content/file … /blacksmith_sp22.pdf
Citation: Serious information vulnerabilities successful DRAM representation devices (2021, November 16) retrieved 16 November 2021 from https://techxplore.com/news/2021-11-vulnerabilities-dram-memory-devices.html
This papers is taxable to copyright. Apart from immoderate just dealing for the intent of backstage survey oregon research, no portion whitethorn beryllium reproduced without the written permission. The contented is provided for accusation purposes only.







 English (US) ·
English (US) ·