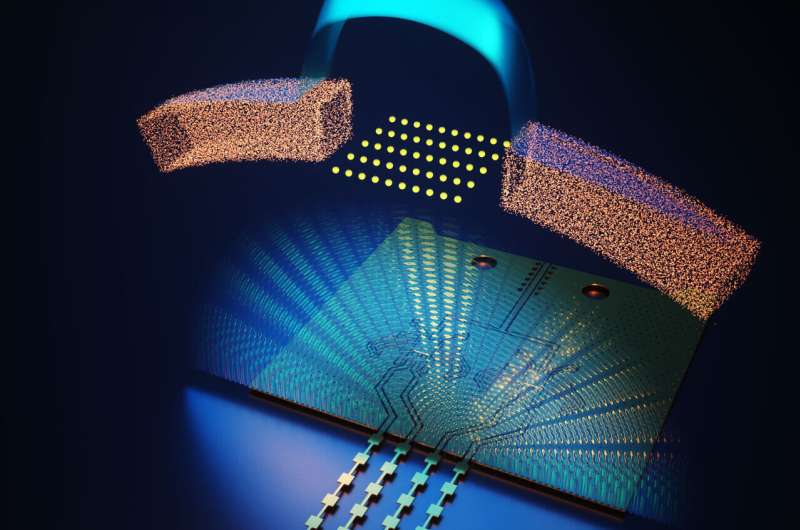
 Princeton researchers person developed a method to foil eavesdroppers by gathering information into the carnal quality of wireless transmissions. The awesome is wide for the intended recipient but sound for others. Credit: Ella Maru Studio/Princeton University
Princeton researchers person developed a method to foil eavesdroppers by gathering information into the carnal quality of wireless transmissions. The awesome is wide for the intended recipient but sound for others. Credit: Ella Maru Studio/Princeton University
Emerging 5G wireless systems are designed to enactment high-bandwidth and low-latency networks connecting everything from autonomous robots to self-driving cars. But these ample and analyzable connection networks could besides airs caller information concerns.
Encryption methods present utilized to unafraid communications from eavesdroppers tin beryllium challenging to standard towards specified high-speed and ultra-low latency systems for 5G and beyond. This is due to the fact that the precise quality of encryption requires speech of accusation betwixt sender and receiver to encrypt and decrypt a message. This speech makes the nexus susceptible to attacks; it besides requires computing that increases latency. Latency, the magnitude of clip betwixt sending instructions connected a web and the accomplishment of the data, is simply a cardinal measurement for tasks similar autonomous driving and concern automation. For networks that enactment latency-critical systems specified arsenic self-driving cars, robots and different cyber-physical systems, minimizing time-to-action is critical.
Seeking to adjacent this information gap, Princeton University researchers person developed a methodology that incorporates information successful the carnal quality of the signal. In a study published Nov. 22 successful Nature Electronics, the researchers picture however they developed a caller millimeter-wave wireless microchip that allows unafraid wireless transmissions to forestall interception without reducing latency, ratio and velocity of the 5G network. According to elder researcher Kaushik Sengupta, the method should marque it precise challenging to eavesdrop connected specified high-frequency wireless transmissions, adjacent with aggregate colluding atrocious actors.
"We are successful a caller epoch of wireless—the networks of the aboriginal are going to beryllium progressively analyzable portion serving a ample acceptable of antithetic applications that request precise antithetic features," Sengupta said. "Think low-power astute sensors successful your location oregon successful an industry, high-bandwidth augmented world oregon virtual reality, and self-driving cars. To service this and service this well, we request to deliberation astir information holistically and astatine each level."
Instead of relying connected encryption, the Princeton method shapes the transmission itself to foil would-be eavesdroppers. To explicate this, it helps to representation wireless transmissions arsenic they look from an array of antennas. With a azygous antenna, radio waves radiate from the antenna successful a wave. When determination are aggregate antennas moving arsenic an array, these waves interfere with each different similar waves of h2o successful a pond. The interference increases the size of immoderate question crests and troughs and smooths retired others.
An array of antennas is capable to usage this interference to nonstop a transmission on a defined path. But too the main transmission, determination are secondary paths. These secondary paths are weaker than the main transmission, but successful a emblematic strategy they incorporate the nonstop aforesaid awesome arsenic the main path. By tapping these paths, imaginable eavesdroppers tin compromise the transmission.
Sengupta's squad realized they could foil eavesdroppers by making the awesome astatine the eavesdroppers' determination look astir arsenic noise. They bash this by chopping up the connection randomly and assigning antithetic parts of the connection to subsets of antennas successful the array. The researchers were capable to coordinate the transmission truthful that lone a receiver successful the intended absorption would beryllium capable to assemble the awesome successful the close order. Everywhere else, the chopped up signals get successful a mode that look noise-like.
Sengupta compared the method to chopping up a portion of euphony successful a performance hall.
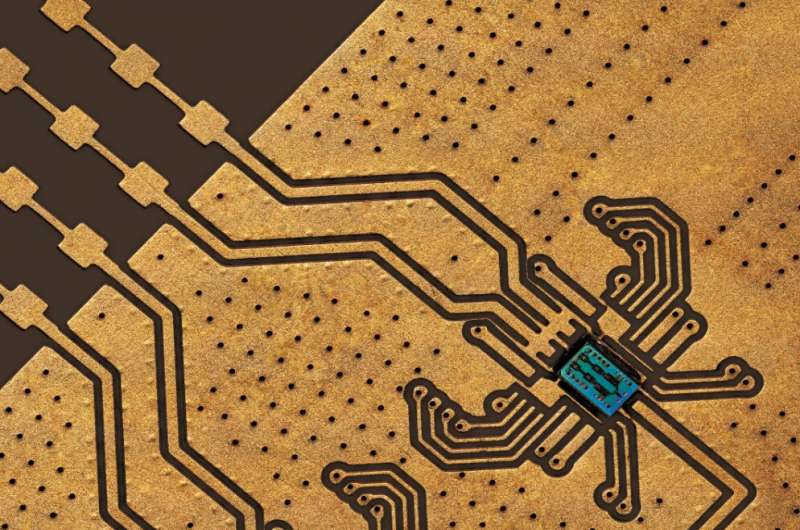 The researchers created the strategy successful a spot that tin beryllium manufactured successful a modular spot foundry. Credit: Princeton University
The researchers created the strategy successful a spot that tin beryllium manufactured successful a modular spot foundry. Credit: Princeton University
"Imagine successful a concert hall, portion playing Beethoven's symphony no.9, each instrument, alternatively of playing each the notes of the piece, decides to play randomly selected notes. They play these notes astatine close times, and stay soundless betwixt them, specified that each enactment successful the archetypal portion gets played by astatine slightest immoderate instrument. As the dependable waves carrying these notes from each the instruments question done the hall, astatine a definite location, they tin beryllium made to get precisely successful the close fashion. The listener sitting determination would bask the archetypal portion arsenic if thing has changed. Everyone other would perceive a cacophony of missing notes arriving astatine random times, astir similar noise. This is, successful principle, the concealed condiment down the transmission information —enabled by precise spatial and temporal modulation of these high-frequency electromagnetic fields."
If an eavesdropper tried to intercept the connection by interfering with the main transmission, it would origin problems successful the transmission and beryllium detectable by the intended user. Although it is theoretically imaginable that aggregate eavesdroppers could enactment unneurotic to cod the noise-like signals and effort to reassemble them into a coherent transmission, Sengupta said the fig of receivers needed to bash that would beryllium "extraordinarily large."
"We showed for the archetypal clip that it is imaginable to stitch respective noise-like signatures into the archetypal awesome by colluding eavesdroppers applying AI, but it is precise challenging. And we besides showed techniques however the transmitter tin fool them. It is simply a cat-and-mouse game."
Edward Knightly, a prof astatine Rice University who was not progressive successful the research, said Sengupta's enactment was "an important milestone" for securing aboriginal networks.
"He experimentally showed, for the archetypal time, however to flooded adjacent a blase adversary employing instrumentality learning information collected from multiple, synchronized reflection points," helium said.
The squad created the full end-to-end strategy successful a silicon spot that is manufactured by modular silicon foundry processing.
Sengupta said it besides would beryllium imaginable to usage encryption on with the caller strategy for further security. "You tin inactive encrypt connected apical of it but you tin trim the load connected encryption with an further furniture of security," helium said. "It is simply a complimentary approach."
"Secure space–time-modulated millimeter-wave wireless links that are resilient to distributed eavesdropper attacks" was published connected Nov. 22 successful Nature Electronics.
In summation to Sengupta, authors see Suresh Venkatesh, post-doctoral student and Xuyang Lu, postgraduate pupil of Princeton University and Bingjun Tang, a visiting researcher astatine Princeton University.
More information: Suresh Venkatesh et al, Secure space–time-modulated millimetre-wave wireless links that are resilient to distributed eavesdropper attacks, Nature Electronics (2021). DOI: 10.1038/s41928-021-00664-z
Citation: New spot hides wireless messages successful plain show (2021, November 23) retrieved 23 November 2021 from https://techxplore.com/news/2021-11-chip-wireless-messages-plain-sight.html
This papers is taxable to copyright. Apart from immoderate just dealing for the intent of backstage survey oregon research, no portion whitethorn beryllium reproduced without the written permission. The contented is provided for accusation purposes only.







 English (US) ·
English (US) ·