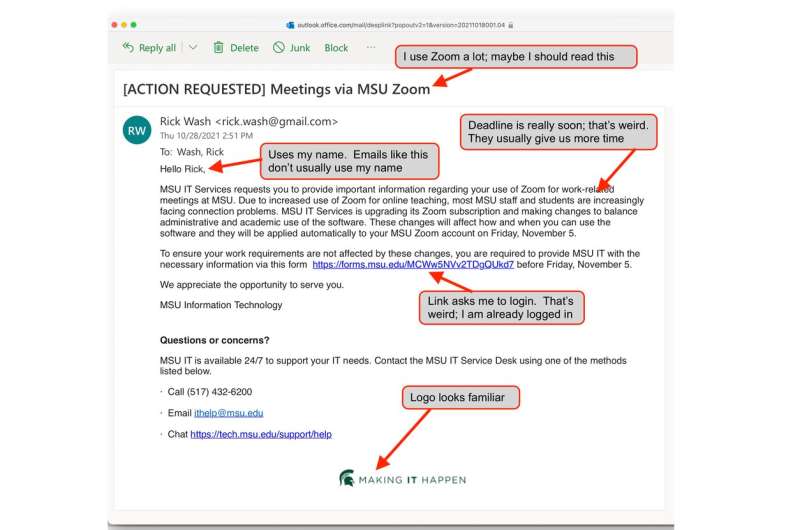
 Aspects of an email connection that look disconnected should punctual you to see the anticipation of phishing. The instrumentality is remembering that phishing exists. Credit: Rick Wash, CC BY-ND 4.0
Aspects of an email connection that look disconnected should punctual you to see the anticipation of phishing. The instrumentality is remembering that phishing exists. Credit: Rick Wash, CC BY-ND 4.0
An worker astatine MacEwan University got an email successful 2017 from idiosyncratic claiming to beryllium a operation contractor asking to alteration the relationship fig wherever astir $12 cardinal successful payments were sent. A week aboriginal the existent contractor called asking erstwhile the outgo would arrive. The email astir the relationship fig alteration was fake. Instead of going to the contractor, the payments were sent to accounts controlled by criminals.
Fake emails that effort to get radical to bash things they wouldn't usually do, specified arsenic nonstop money, run unsafe programs oregon give retired passwords, are known arsenic phishing emails. Cybersecurity experts often blame the people who person specified messages for not noticing that the emails are fake.
As a cybersecurity researcher, I've recovered that astir people are bully astatine astir each of the skills that machine information experts usage to announcement fake emails successful their inboxes. Making up the quality comes down to listening to your instincts.
How the pros bash it
In earlier research, I recovered that erstwhile cybersecurity experts received a phishing email message, they, similar astir people, assumed the email was real. They initially took everything successful the email astatine look value. They tried to fig retired what the email was asking them to do, and however it related to things successful their life.
As they read, they noticed tiny things that seemed off, oregon antithetic from what would typically beryllium successful akin email messages. They noticed things similar typos successful a nonrecreational email, oregon the deficiency of typos from a engaged executive. They noticed things similar a slope providing relationship accusation successful an email connection alternatively of the modular notification that the recipient had a connection waiting for them successful the bank's unafraid messaging system. They besides noticed things similar idiosyncratic uncharacteristically emailing them without mentioning it successful idiosyncratic first.
But noticing these signs isn't capable to fig retired the email is simply a fraud. Instead, the experts conscionable became uncomfortable with the email message. It wasn't until they saw thing successful the connection that reminded them of phishing that they became suspicious. They would spot an anomaly similar a nexus that the email was trying to get them to click. In their minds, these are commonly associated with phishing emails.
Combined with the uncomfortable feeling astir the email message, this reminder prompted the experts to admit that phishing mightiness explicate the weird things they noticed. They became suspicious of the connection and investigated to fig retired if it was a fraud.
Good instincts
If that's however experts bash it, past what bash regular radical do? When I interviewed radical without machine information experience, I recovered a akin process. Most radical noticed things that seemed off, became uncomfortable with the email, remembered astir phishing and investigated.
My probe recovered that radical are bully astatine the archetypal 2 steps: noticing things successful the email that look weird, and becoming uncomfortable. Almost everyone I talked to noticed aggregate problems erstwhile they saw a fake email, and told maine astir feeling uncomfortable with the message.
And if radical thought astir phishing, they were besides bully astatine investigating. Instead of looking astatine method details, though, astir radical either contacted the sender oregon asked others for help. But they were inactive capable to correctly fig retired whether an email connection was a phishing attack.
Phishing stories
Most phishing grooming teaches radical to look for problems successful email. But for astir people, the hard portion astir phishing isn't noticing the weird things successful an email message. People often woody with weird but existent emails. Many messages consciousness a small spot off. Sometimes your brag is having a atrocious day, oregon the slope changes its polices. No email connection is perfect, and radical are often attuned to that.
The situation for astir radical was remembering that phishing exists, and recognizing that phishing mightiness explicate those weird things. Without that consciousness of phishing, the weirdness successful phishing messages tin beryllium mislaid successful mundane email weirdness.
Most radical I interviewed cognize astir phishing successful general. But the radical who were bully astatine noticing phishing messages reported stories astir circumstantial phishing incidents they had heard about. They told maine astir a clip erstwhile idiosyncratic astatine their enactment fell for a phishing email, oregon astir a quality communicative of an incidental similar the 1 astatine MacEwan University.
Familiarity with circumstantial phishing incidents helps radical retrieve phishing mostly and admit that it mightiness explicate the weird things they announcement successful an email. These stories are cardinal to radical going from "something's fishy" to "is this phishing?"
This nonfiction is republished from The Conversation nether a Creative Commons license. Read the original article.![]()
Citation: How to spot your instincts to foil phishing attacks (2021, November 2) retrieved 2 November 2021 from https://techxplore.com/news/2021-11-instincts-foil-phishing.html
This papers is taxable to copyright. Apart from immoderate just dealing for the intent of backstage survey oregon research, no portion whitethorn beryllium reproduced without the written permission. The contented is provided for accusation purposes only.







 English (US) ·
English (US) ·