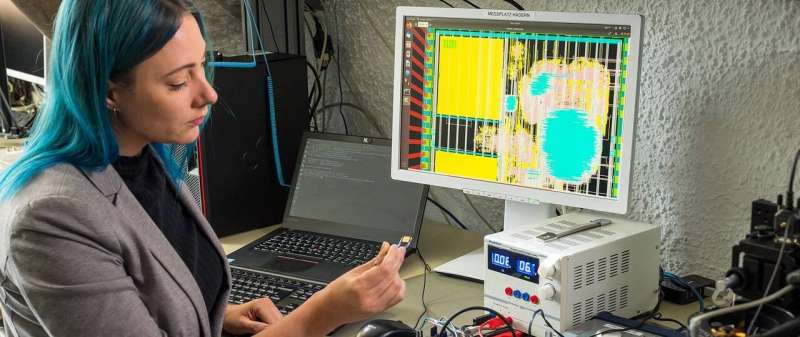
 A squad astatine the Chair of Security successful Information Technology has developed a spot with peculiarly unafraid encryption technology. Johanna Baehr heads a 2nd squad astatine the seat that has hidden 4 hardware Trojans connected this spot - malicious functions that are integrated straight into the circuits. Credit: Astrid Eckert / TUM
A squad astatine the Chair of Security successful Information Technology has developed a spot with peculiarly unafraid encryption technology. Johanna Baehr heads a 2nd squad astatine the seat that has hidden 4 hardware Trojans connected this spot - malicious functions that are integrated straight into the circuits. Credit: Astrid Eckert / TUM
A squad astatine the Technical University of Munich (TUM) has designed and commissioned the accumulation of a machine spot that implements post-quantum cryptography precise efficiently. Such chips could supply extortion against aboriginal hacker attacks utilizing quantum computers. The researchers besides incorporated hardware Trojans successful the spot successful bid to survey methods for detecting this benignant of "malware from the spot factory."
Hacker attacks connected concern operations are nary longer subject fiction—far from it. Attackers tin bargain accusation connected accumulation processes oregon unopen down full factories. To forestall this, connection betwixt the chips successful the idiosyncratic components is encrypted. Before long, however, galore encryption algorithms volition go ineffective. The established processes that tin combat disconnected attacks launched with today's machine technologies volition beryllium defenseless against quantum computers. This is particularly captious for instrumentality with a agelong lifespan specified arsenic concern facilities.
For this reason, information experts astir the satellite are moving to make method standards for "post-quantum cryptography." One of the challenges is posed by the tremendous processing powerfulness needed for these encryption methods. A squad moving with Georg Sigl, Professor of Security successful Information Technology astatine TUM, has present designed and commissioned a highly businesslike spot for post-quantum cryptography.
Speed and flexibility done a operation of hardware and software
Professor Sigl and his squad took an attack based connected hardware/software co-design, successful which specialized components and the power bundle complement 1 another. "Ours is the archetypal spot for post-quantum cryptography to beryllium based wholly connected a hardware/software co-design approach," says Prof. Sigl.
"As a result, it is astir 10 times arsenic accelerated erstwhile encrypting with Kyber—one of the astir promising candidates for post-quantum cryptography—as compared to chips based wholly connected bundle solutions. It besides uses astir 8 times little vigor and is astir arsenic flexible."
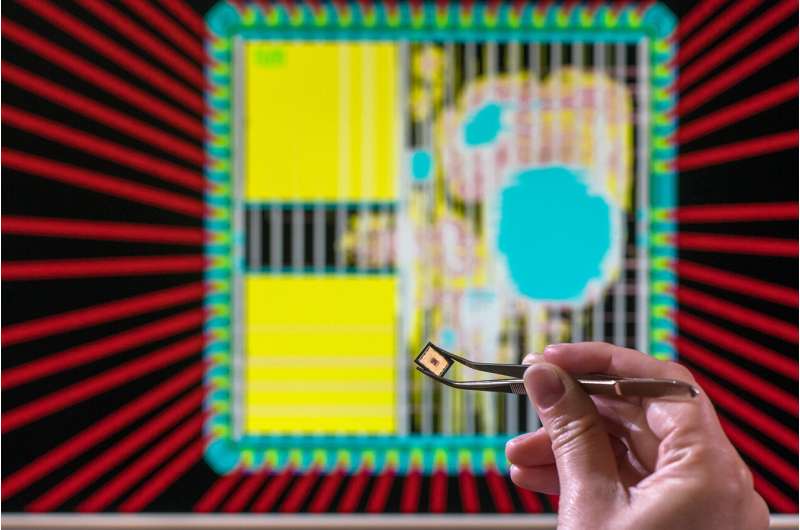 The spot relies connected a choky operation of hardware and bundle to use post-quantum encryption performant and energy-efficiently. Credit: Astrid Eckert / TUM
The spot relies connected a choky operation of hardware and bundle to use post-quantum encryption performant and energy-efficiently. Credit: Astrid Eckert / TUM
Based connected an unfastened root standard
The spot is an application-specific integrated circuit (ASIC). This benignant of specialized microcontroller is often manufactured successful ample numbers according to specifications of companies. The TUM squad modified an unfastened root spot plan based connected the unfastened root RISC-V standard. It is utilized by expanding numbers of spot makers and could regenerate proprietary approaches of large companies successful galore areas. The chip's post-quantum cryptography capabilities are facilitated by a modification of the processor halfway and peculiar instructions that velocity up the indispensable arithmetic operations.
The plan besides incorporates a purpose-designed hardware accelerator. It not lone supports lattice-based post-quantum cryptography algorithms specified arsenic Kyber, but could besides enactment with the SIKE algorithm, which requires overmuch much computing power. According to the team, the spot developed astatine TUM could instrumentality SIKE 21 times faster than chips utilizing lone software-based encryption. SIKE is seen arsenic the astir promising alternate if the clip comes erstwhile lattice-based approaches are nary longer secure. Precautions of this benignant marque consciousness successful applications wherever chips volition beryllium utilized for extended periods.
Hardware Trojans evade post-quantum cryptography
Another imaginable threat, alongside the emergence successful accepted attacks, is posed by hardware Trojans. Computer chips are mostly produced according to companies' specifications and made successful specialized factories. If attackers win successful planting trojan circuitry successful the spot plan earlier oregon during the manufacturing stage, this could person disastrous consequences. As successful the lawsuit of outer hacker attacks, full factories could beryllium unopen down oregon accumulation secrets stolen. What's more: Trojans built into the hardware tin evade post-quantum cryptography.
"We inactive cognize precise small astir however hardware trojans are utilized by existent attackers," explains Georg Sigl. "To make protective measures, we request to deliberation similar an attacker and effort to make and conceal our ain Trojans. In our post-quantum spot we person truthful developed and installed 4 hardware Trojans, each of which works successful an wholly antithetic way."
Chip to beryllium tested and past dismantled
Over the coming months, Prof. Sigl and his squad volition intensively trial the chip's cryptography capabilities and functionality and the detectability of the hardware trojans. The spot volition past beryllium destroyed—for probe purposes. In a analyzable process, the circuit pathways volition beryllium shaved disconnected incrementally portion photographing each successive layer. The extremity is to effort retired caller instrumentality learning methods developed astatine Prof. Sigl's seat for reconstructing the precise functions of chips adjacent erstwhile nary documentation is available. "These reconstructions tin assistance to observe spot components that execute functions unrelated to the chip's existent tasks and which whitethorn person been smuggled into the design," says Georg Sigl. "Processes similar ours could go the modular for taking random samples successful ample orders of chips. Combined with effectual post-quantum cryptography, this could assistance america to marque hardware much secure—in concern facilities arsenic good arsenic successful cars."
More information: Alexander Hepp et al, Tapeout of a RISC-V crypto spot with hardware trojans, Proceedings of the 18th ACM International Conference connected Computing Frontiers (2021). DOI: 10.1145/3457388.3458869
Debapriya Basu Roy et al, Efficient hardware/software co-design for post-quantum crypto algorithm SIKE connected ARM and RISC-V based microcontrollers, Proceedings of the 39th International Conference connected Computer-Aided Design (2020). DOI: 10.1145/3400302.3415728
Fritzmann, T. et al, J. RISQ-V: Tightly Coupled RISC-V Accelerators for Post-Quantum Cryptography. IACR Transactions connected Cryptographic Hardware and Embedded Systems (2020). DOI: 10.13154/tches.v2020.i4.239-280
Citation: Chip with unafraid encryption volition assistance successful combat against hackers (2021, August 4) retrieved 4 August 2021 from https://techxplore.com/news/2021-08-chip-encryption-hackers.html
This papers is taxable to copyright. Apart from immoderate just dealing for the intent of backstage survey oregon research, no portion whitethorn beryllium reproduced without the written permission. The contented is provided for accusation purposes only.







 English (US) ·
English (US) ·