 Illustration of a BrakTooth onslaught scenario. Credit: SUTD
Illustration of a BrakTooth onslaught scenario. Credit: SUTD
Researchers from the Singapore University of Technology and Design (SUTD) released 16 caller information vulnerabilities, with the codename BrakTooth, affecting a wide scope of Bluetooth classical (BR/EDR) implementations. The report, done successful collaboration with the Institute for Infocomm Research (I2R), Agency for Science, Technology and Research (A*STAR), was led by Assistant Professor Sudipta Chattopadhyay from SUTD's ASSET (Automated Systems SEcuriTy) Research Group.
In the white paper titled "BrakTooth: Causing Havoc connected Bluetooth Link Manager," it was noted that the vulnerabilities affected large Bluetooth chipset vendors including Intel, Qualcomm, Texas Instruments, Infineon (Cypress) and Silicon Labs. The scope of these vulnerabilities are apt to impact mostly mainstream physics instrumentality users owed to their dense usage of laptops and smartphones successful their day-to-day life. More specifically, large laptop vendors from Microsoft, Asus, Dell, and HP etc. are utilizing the affected Intel chipset (Intel AX200). Concurrently, the affected Qualcomm chipsets (WCN3990/8) are utilized by large smartphones and tablet vendors specified arsenic Samsung, Sony and Xiaomi.
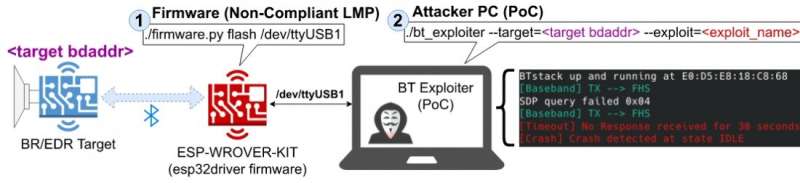
The probe squad has clarified that the reported vulnerabilities let an attacker to remotely unopen down a Bluetooth enabled device. For example, definite vulnerabilities let an attacker to remotely shutdown a headset oregon speaker. This means erstwhile a idiosyncratic is listening to audio from a laptop utilizing the headset oregon speaker, they tin acquisition the audio being chopped abruptly. The attacks tin beryllium launched continuously, which, successful crook tin impair the user's listening experience.
The astir superior vulnerability reported by the probe squad allows for arbitrary codification execution successful an embedded controller. An arbitrary codification execution allows an attacker to remotely execute attacker chosen codification successful the people device. For example, the reported vulnerability allows the attacker to remotely delete each information successful the people devices' memory. Apart from affecting astir large laptops, smartphones and tablets, the vulnerabilities besides interaction a scope of different products for instance, the manufacture automation, automotive infotainment systems, craft amusement systems, speakers and headsets etc.
BrakTooth - Feature Response Flooding connected Audio Products
The probe squad besides highlighted that the Bluetooth listing reports implicit 1,400 products to beryllium affected. However, owed to the constricted hunt capableness successful the Bluetooth listing website, the existent fig of affected products is expected to beryllium an bid of magnitude higher than the fig of listings observed.
Researchers of the reported vulnerabilities followed a liable disclosure process portion reporting the vulnerabilities to vendors. They provided each Bluetooth system-on-chip (SoC) and module vendors astatine slightest 90 days until the nationalist disclosure to hole the vulnerabilities successful their chipsets. However, researchers person reported that patches for these vulnerabilities are lone partially disposable for now.
For instance, patches for Intel and Qualcomm volition lone beryllium disposable astir October 2021. Thus, respective large laptops and smartphones volition beryllium unpatched until the fixes are disposable from Intel and Qualcomm. Researchers besides warned that respective of these vulnerabilities, arsenic reported by the respective vendors specified arsenic Qualcomm, are intolerable to hole owed to the unavailability of abstraction successful the affected chipsets. Thus, immoderate module/product employing specified chipsets are apt to stay susceptible forever. Researchers counsel Bluetooth merchandise vendors to behaviour a thorough hazard appraisal if their merchandise is utilizing definite susceptible chipsets and reconsider their plan if the hazard is not acceptable.
The probe squad understands the hazard successful releasing the onslaught codification (exploits) arsenic galore devices stay susceptible to BrakTooth attacks arsenic of today. However, immoderate Bluetooth SoC and module vendors tin get entree to the onslaught codification to measure the information of their instrumentality here: poc.braktooth.com .
Citation: Bluetooth devices proven to beryllium susceptible to unfixable information problems (2021, September 1) retrieved 1 September 2021 from https://techxplore.com/news/2021-09-bluetooth-devices-proven-vulnerable-unfixable.html
This papers is taxable to copyright. Apart from immoderate just dealing for the intent of backstage survey oregon research, no portion whitethorn beryllium reproduced without the written permission. The contented is provided for accusation purposes only.







 English (US) ·
English (US) ·